Procyon Blog
Everything you need to know about cloud and user identity
Identity and access management traces its roots back to the mainframe era. DoD first employed logical...
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology....
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now...
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly...
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become...
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we...
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to...
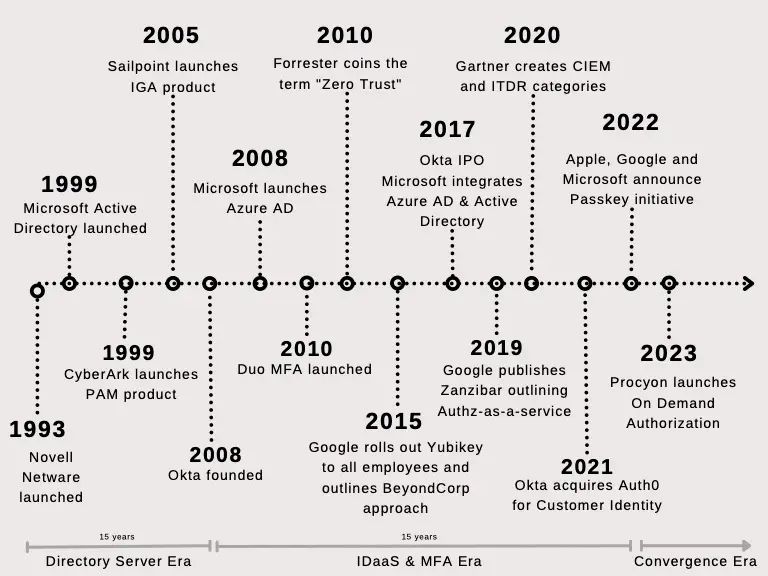
Evolution of modern identity stack
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and...
Passkeys and Security 2.0 concepts
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology. Passkey is a friendly brand...
Code to cloud: verifiable deployments
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now famous Turing award acceptance...
Workload Identity in Security 2.0 Stack
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly privileged human users. In this post...
Privileged users in Security 2.0 Stack
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become the source of a software...
Security 2.0
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we include all the packages we import...
Procyon Achieves SOC 2 Type 2 Compliance, Signifying Commitment to Data Security and Client Trust
[San Jose, CA, October 20th, 2023] — Procyon, a leading provider of next generation cloud-based privilege access management solution, is...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
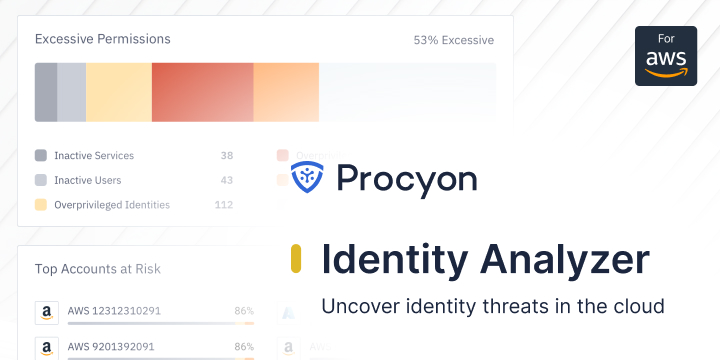
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Evolution of modern identity stack
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and...
Passkeys and Security 2.0 concepts
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology. Passkey is a friendly brand...
Code to cloud: verifiable deployments
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now famous Turing award acceptance...
Workload Identity in Security 2.0 Stack
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly privileged human users. In this post...
Privileged users in Security 2.0 Stack
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become the source of a software...
Security 2.0
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we include all the packages we import...
Procyon Achieves SOC 2 Type 2 Compliance, Signifying Commitment to Data Security and Client Trust
[San Jose, CA, October 20th, 2023] — Procyon, a leading provider of next generation cloud-based privilege access management solution, is...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Evolution of modern identity stack
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and...
Passkeys and Security 2.0 concepts
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology. Passkey is a friendly brand...
Code to cloud: verifiable deployments
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now famous Turing award acceptance...
Workload Identity in Security 2.0 Stack
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly privileged human users. In this post...
Privileged users in Security 2.0 Stack
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become the source of a software...
Security 2.0
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we include all the packages we import...
Procyon Achieves SOC 2 Type 2 Compliance, Signifying Commitment to Data Security and Client Trust
[San Jose, CA, October 20th, 2023] — Procyon, a leading provider of next generation cloud-based privilege access management solution, is...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Evolution of modern identity stack
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and...
Passkeys and Security 2.0 concepts
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology. Passkey is a friendly brand...
Code to cloud: verifiable deployments
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now famous Turing award acceptance...
Workload Identity in Security 2.0 Stack
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly privileged human users. In this post...
Privileged users in Security 2.0 Stack
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become the source of a software...
Security 2.0
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we include all the packages we import...
Procyon Achieves SOC 2 Type 2 Compliance, Signifying Commitment to Data Security and Client Trust
[San Jose, CA, October 20th, 2023] — Procyon, a leading provider of next generation cloud-based privilege access management solution, is...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...