Enhanced Protection – Terminate Live Sessions Instantly
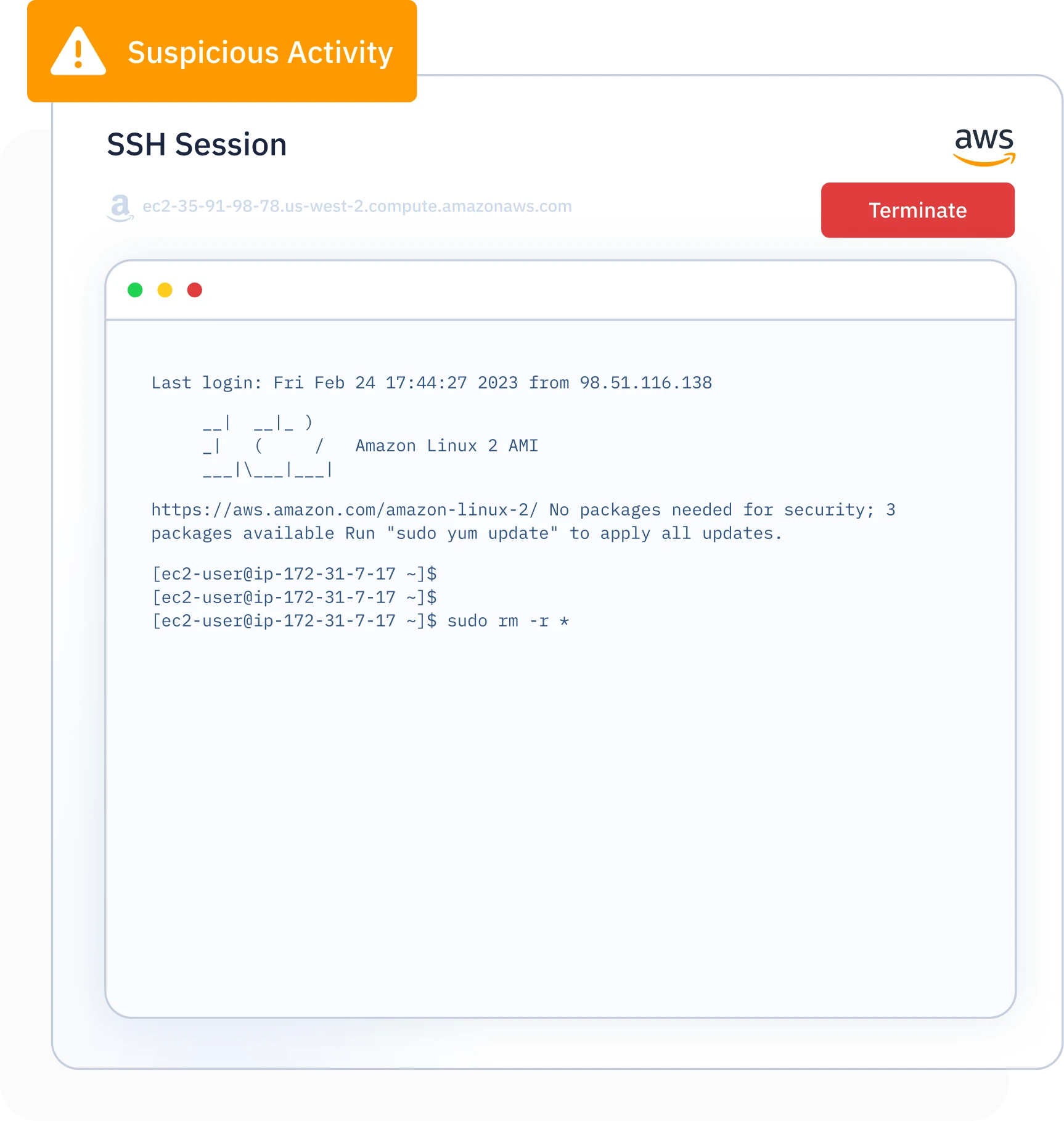
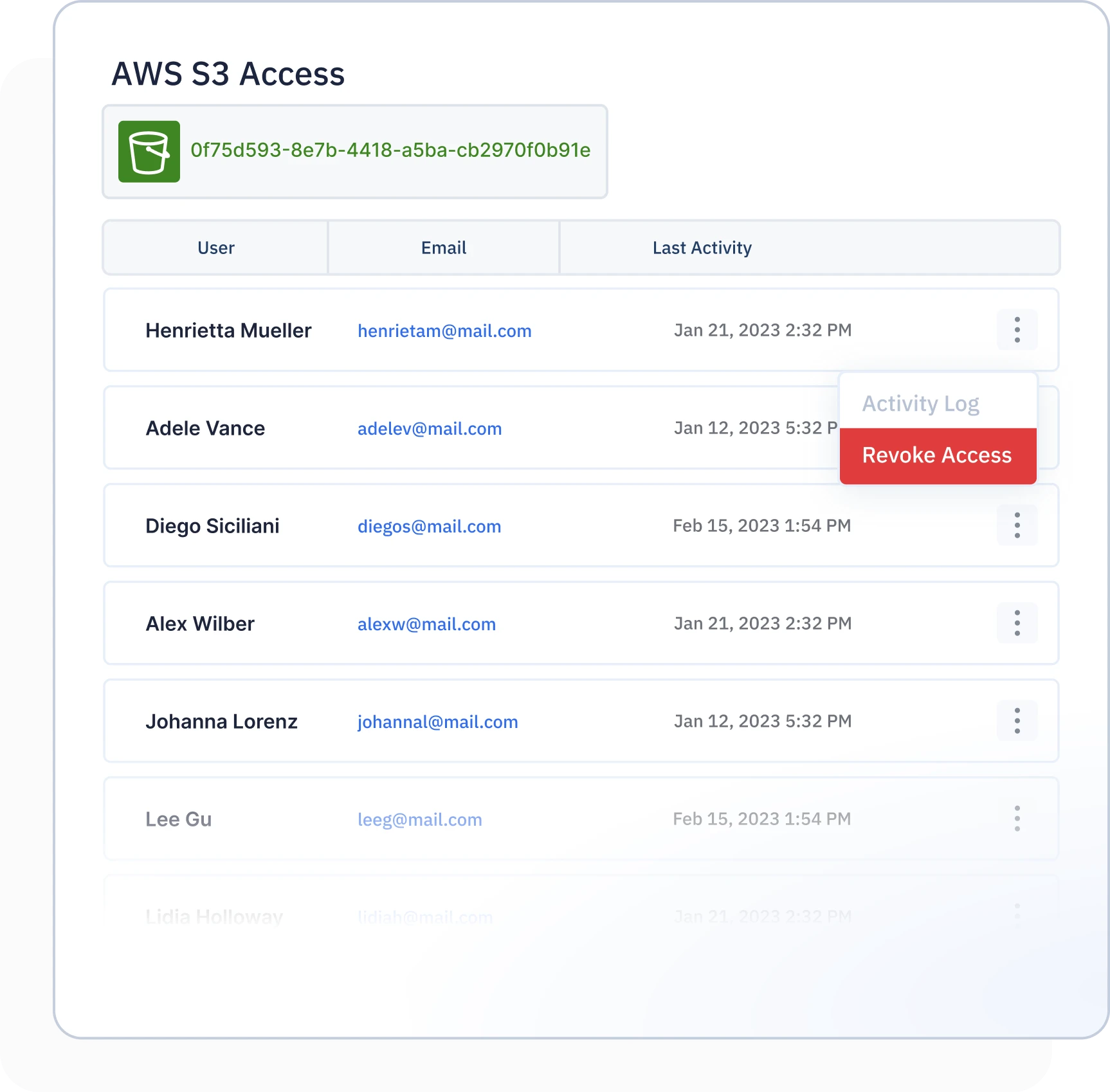
Stop Malicious Access
Access Revocation
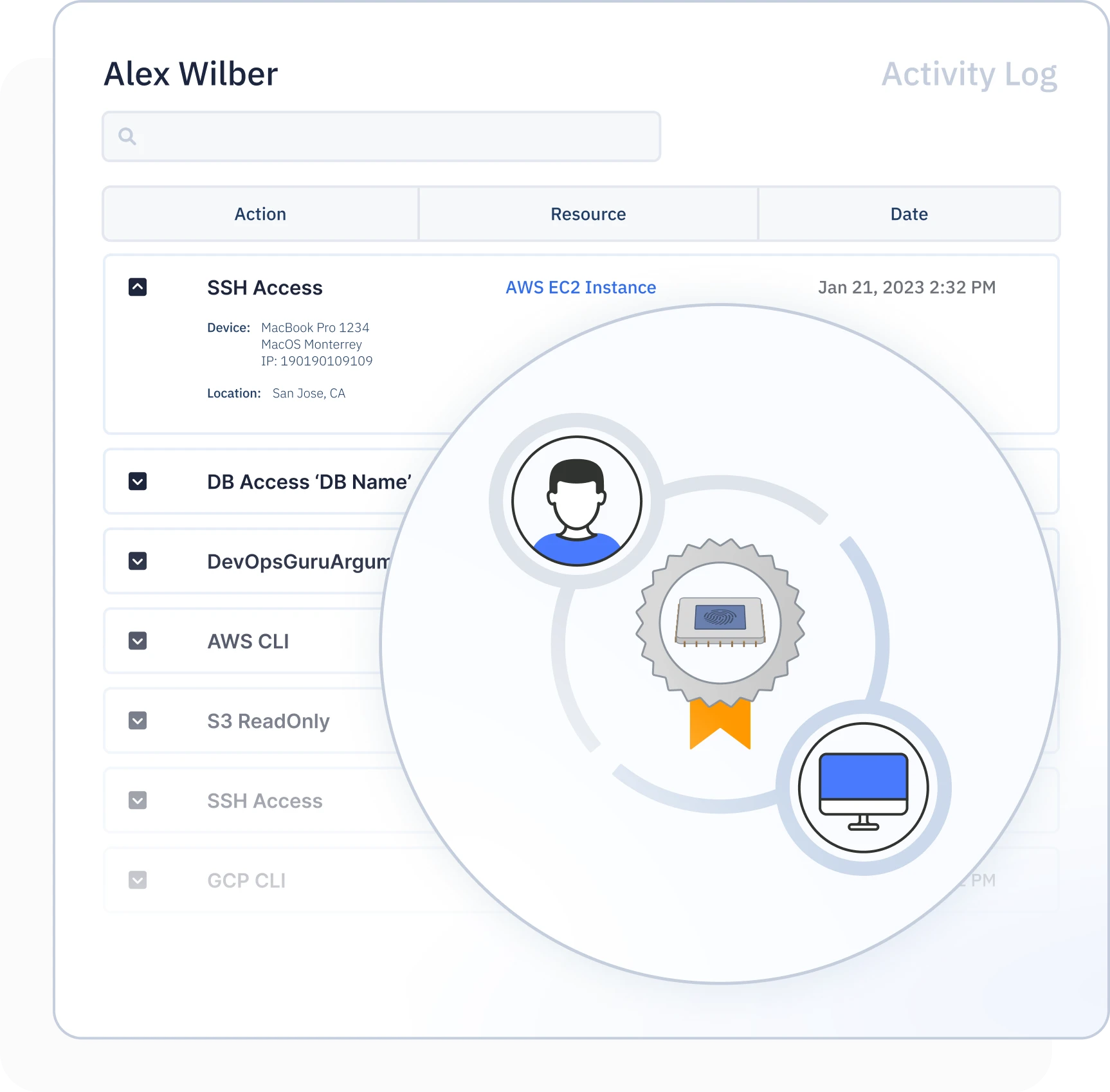
Strong User and Device Identity
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.
Recent Resources
Identity and access management traces its roots back to the mainframe era. DoD first employed logical...
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology....
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now...
Get in touch
Want to know more about our product? Please fill out the form and share your message with us.
- Request a demo
- Business tiers and pricing
- General questions