Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and discretionary access control(MAC/DAC). This eventually evolved into what we now call Role Based Access Control(RBAC). More modern identity stack evolved in two distinct phases. First as a directory service starting with Novell Netware in early 90s before Microsoft Active Directory took over as the de-facto standard in most enterprises. Second phase as SSO and MFA became the mainstay especially with the evolution of SaaS services. You can call this IDaaS phase as the modern cloud based directory services are now called. In this post we will outline the evolution of the modern identity stack and discuss what the future may hold.
Directory Server Era
The PCs became popular in the enterprises in the 80s. By the 90s most enterprises were interconnecting them into a corporate network. When they interconnected, the users wanted to share files between computers. Having different credentials for each file share became a problem. Novell solved this problem with their Netware product. This was the birth of corporate wide directory services. In the late 90s Microsoft launched Active Directory along with the Domain controller. It provided a way for organizations to authenticate and authorize users centrally and set organization wide policies like password policies. It also allowed the admins to configure and manage a fleet of windows PCs from a central point. In a few years Active Directory became widely adopted and the Netware product was dead.
This era also saw the creation of two other identity related product categories IGA and PAM. In the late nineties administrators wanted a way to vault the admin user passwords for multiple systems and share them with other administrators. CyberArk launched a password vault product to store them securely and share them securely. This created a category of product which we now call Privileged Access Management(PAM). In the early 2000s congress passed Sarbanes-Oxley Act (SOX) which required IT teams to establish controls on information access rights and audit user activity. Sailpoint launched its IGA product in 2005 to help the large enterprises solve this problem and establish governance controls.
In the late 90s and early 2000s as the enterprises moved their internal applications to web instead of desktop, it created a need for users to login to internal web applications using consistent password. This created the Web Access Management(WAM) category of products. CA Siteminder is the most well known product in this category. Later the SAML standard became the de-facto standard in the enterprise so that users don’t have to login to each application separately and make use of Single-Sign-On(SSO). Ping Identity, which was established in 2002 became a popular SSO solution. While WAM solutions used proprietary authentication APIs, SAML standardized this API between the applications and Identity Providers. These Identity providers were typically hosted inside the corporate networks behind the firewalls and typically linked to Active Directory so that users could use the same passwords to login to all web applications.
IDaaS and MFA Era
Late 2000s and early 2010s saw the emergence of SaaS applications. IT teams needed a way to link the SaaS applications to their SSO Identity providers. But linking SaaS applications to SSO providers behind the firewall was clunky and the integrations were not seamless. Microsoft’s Active Directory Federation Service was notoriously hard to use. Okta started in 2008 and launched its first product in 2010 to solve this problem of linking SaaS applications to Active Directory behind the firewalls. Okta pre-integrated most of the popular SaaS applications which made it easy for IT teams to quickly link all SaaS applications. Microsoft launched the Azure AD solution in 2008. But it was a standalone SSO solution tied to Microsoft’s Azure offering and did not integrate well with on-premise Active Directory till 2015. Okta called its cloud based identity provider solution as IDentity-as-a-Service(IDaaS) and it’s a pretty good description of their approach to identity management.
In the early 2010s password spraying and credential stuffing attacks became widespread problems. Users were using very simple and easily guessable passwords. They were also reusing the same password across web services. This allowed attackers to easily compromise user’s accounts. This led to the widespread adoption of Multi Factor Authentication technologies. OTP based second factor authentication existed since the mid 90s. RSA SecureID was a hardware OTP token that would generate a new random token every 60 seconds. There were also software based soft-token applications in the market. With the advent of smartphones, we could use the smartphones for MFA authentication. Duo started in 2010 to provide mobile app based second factor authentication. They had both an OTP option and a mobile push option which was convenient for the users. They provided easy integration options for vendors to integrate Duo into their solution. Duo and similar mobile MFA solutions were widely adopted in the 2010s. Cisco bought Duo in 2018. Meanwhile ID providers like Okta and Azure AD also rolled out their own mobile MFA solutions.
Our discussion of the identity stack will not be complete without mentioning Google. They made some important contributions to the evolution of the identity stack. Operation Aurora was a series of cyberattacks conducted by an APT group with ties to the Chinese army. Google announced in 2010 that they were one of the victims of this attack. In 2013 Snowden leaks showed that the NSA had infiltrated inside Google data centers. Google set out to protect themselves from the sophisticated nation state hackers. First they rolled out FIDO2 standard based Yubikey to all its employees to prevent employee identities from being compromised. Next they built “BeyondCorp” which provides identity based access to Google’s internal systems. They also tied the access decisions to endpoint device health using an EDR solution. This ensured only the trusted Google employees could access Google’s internal systems. Third, they created LOAS(Low Overhead Authentication System) which is a cryptographic key distribution system that helps establish workload identity for all workloads running inside Google’s data center. This encrypted all internal communications inside the google datacenter and made sure only the trusted workloads could access data inside google datacenter. The SPIFFE standard is the public version of the workload identity loosely based on similar efforts at Google, Facebook and Netflix. Google’s internal efforts outlined above is one of the best defensive cybersecurity architecture to date. No significant breaches have been reported at Google since they rolled out these three initiatives.
Forrester analysts coined the term “ZeroTrust” in 2010 to describe an approach to cybersecurity that does not trust anyone or anything on the network by default. It has come to mean an identity based approach to cybersecurity whether it is human identities or non-human identities(like workloads, edge devices etc). It also means users have least-privilege and access is granted based on context(like location, device health). Google’s efforts mentioned above does qualify as one of the first successful ZeroTrust implementations. Increasingly the VPN vendors are calling their solution Zero Trust Network Access. Though most of these solutions are Layer4 micro-tunnels and do not meet the ZeroTrust criteria like the Google’s BeyondCorp effort does. Main difference being the ability to understand the application level protocol and perform per request or per transaction authorization decisions. Similarly many of SASE/SSE vendors also position themselves as ZeroTrust vendors.
Increasingly, Customer identity management(CIAM) is becoming an important part of every enterprise’s Identity stack. Every enterprise from Bank Of America to Macy’s stores have customer user accounts they need to manage. Managing the lifecycle of these identities and protecting them and complying with data privacy requirements are becoming increasingly important. Historically customer identity management was just a feature in application frameworks or middlewares. In the late 2000s, with the emergence of social media platforms, social logins using user’s existing identity became popular. Auth0, JanRain, Gigya, LoginRadius were all started in the early 2010s to solve this problem. Auth0 was later acquired by Okta. It is also worth mentioning OAuth and OpenID Connect(OIDC) standards in this context. The OAuth standard was initially created so that users could authorize third party applications to access their data in a web service(Think LinkedIn wanting to access your Gmail address book) without having to share passwords with a third party application. It slowly evolved into performing social logins using social media accounts like Facebook or LinkedIn. The OpenID Connect standard was published as an extension of the OAuth standard for the purposes of social logins. Today many enterprises use OIDC for identity federation instead of SAML.
As Identity has become the perimeter, Identity has also become the biggest threat vector. Many solutions have popped up to help enterprises detect these identity threats and remediate them. Gartner recognized this by creating the Identity Threat Detection and Response(ITDR) category. Another adjacent segment is Cloud Infrastructure Entitlement Management which is specifically focused on permission management in the IaaS environments.
We briefly mentioned the FIDO2 standard while discussing Google’s rollout of Yubikeys. These provide phishing resistant authentication for human users. We don’t need hardware tokens like Yubikey anymore as most of the end user devices now come with a built-in chip called TPM chips(Apple calls them “Secure Enclave” chips). These built-in chips have the same security properties as a Hardware token. Apple, Google and Microsoft announced support for Passkey in all PCs and smartphones. Passkey is a friendly branding of FIDO2 standard.
In 2019 Google published “Zanzibar” which is their approach to providing Authorization-as-a-Service to their developers so that every team didn’t have to reinvent the wheel on fine grained access controls. Initially this was used by Google docs and Google workspaces teams to manage document sharing. Number of solutions have popped up to offer a similar approach to developers. Open Policy Agent(OPA) existed for a few years before this. Recently Auth0/Okta announced OpenFGA which is their version of Authz-as-a-service.
Another emerging category is non-human identity management. These are things like being able to manage workload identities, edge and IOT device identities. Most enterprises manage 10-50x more non-human identities than human identities. Managing their lifecycle in a consistent and centralized manner has become a priority.
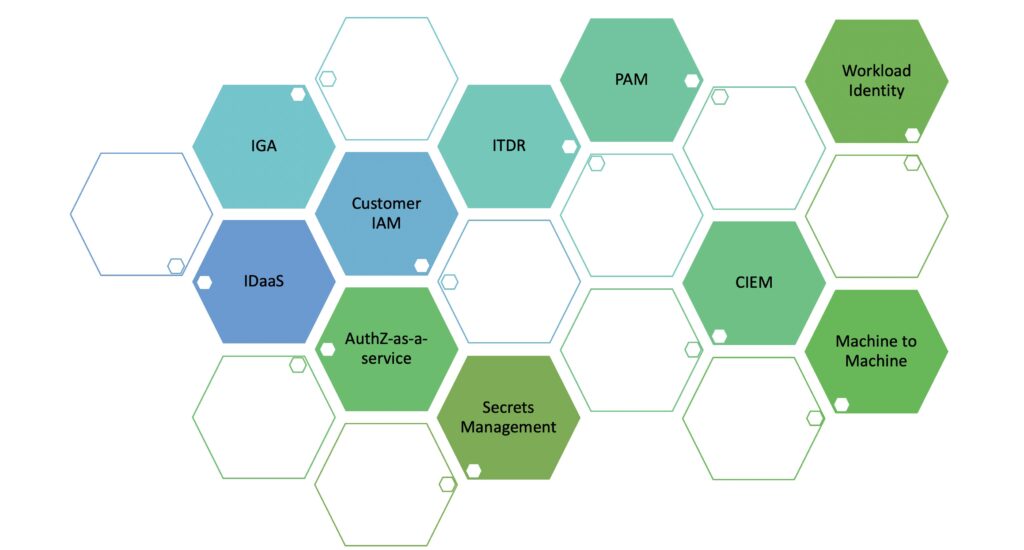
Modern Identity Stack
There used to be a time when IDaaS, IGA and PAM were the only three categories in Identity and Access Management. New categories have emerged as our software stack has evolved and the use cases have evolved. Customer identity management and non-human identity management have become equally important to workforce identity management. We can categorize these new categories roughly in three buckets:
-
Human identity and access management
- IDaaS is the biggest category in human user management. This involves authentication, MFA, Passkey and context aware authentication.
- Identity Governance(IGA) is an important category. This is increasingly dealing with role management across SaaS applications instead of on-premise applications
- Privilege Access Management(PAM) for human users is also an important category. For privileged users in the cloud the line between IGA and PAM is blurring. PAM is increasingly becoming entitlement management for the cloud infrastructure(CIEM) and broader privileged API permissions management.
- Customer Identity management(CIAM) is an important category helping enterprises manage customer identities, federated logins and social logins.
-
Non-human identity and access management.
- Machine to Machine identity management is for managing non-human edge device identities and how they can access enterprise services.
- Workload identity management is for managing cloud workload lifecycle management, federating their identities across multiple clouds and managing their access to other services
- Secrets management is often the glue between more modern applications which support workload identity federation and legacy software like databases which support only credential based access.
-
Identity threat detection
- ITDR solutions help the security teams identify the identity based threats and remediate them. While most other categories mentioned above are deployed by IT teams or developers. ITDR is emerging as the primary tool used by the security teams to detect these threats.
- SaaS Security Posture Management(SSPM) is an adjacent segment to ITDR which focuses on SaaS data security. It focuses on the identity threats in SaaS services, third party applications that have access to data in SaaS services and any data leak threats in SaaS environments. The CASB solutions were supposed to solve these problems. But most CASB solutions are inline and come with their own deployment challenges. SSPM is emerging as an offline API based alternative to CASBs.
What the future holds
In the near future we will see the convergence of identity stacks on both the human user side and non-human user side. On the human users side, we will have convergence of workforce identity, customer identity, fraud management and privacy management stacks. We often like to call this convergence Security 2.0. None of us want to manage 140 different passwords we deal with today, one for every web service we use. None of us want to worry about identity frauds. None of us want our personal data breached. More importantly we don’t want the breached personal data to be used against us in identity frauds. All of us would rather use passkeys to login seamlessly across all services. We might want to have a handful of different personas for work, home and social life. Which also means we don’t want to be managing different passkey accounts for each service with its own recovery mechanisms and onboarding process. Use of passkeys and biometric technologies during authorization will become common both for fraud prevention and cyber attack prevention. We will discuss this part more in detail in the next post in this series. We will likely see the emergence of converged identity stack as-a-service that manages both authentication and authorization using passkeys for human users.
Similarly we will see the emergence of converged non-human user identity federation stack. We will move to a secret-less access model for non-human identities where we are granting access to specific workload, machine or service identity instead of using things like secrets or API tokens.
In the next post in this series we will further explore how the identity stack is evolving in the convergence era and how On Demand Authorization plays a key role in this evolution.