Seamless
Identity-Powered Security
The next generation cloud-based privilege access management solution for multi-cloud identity and access management.
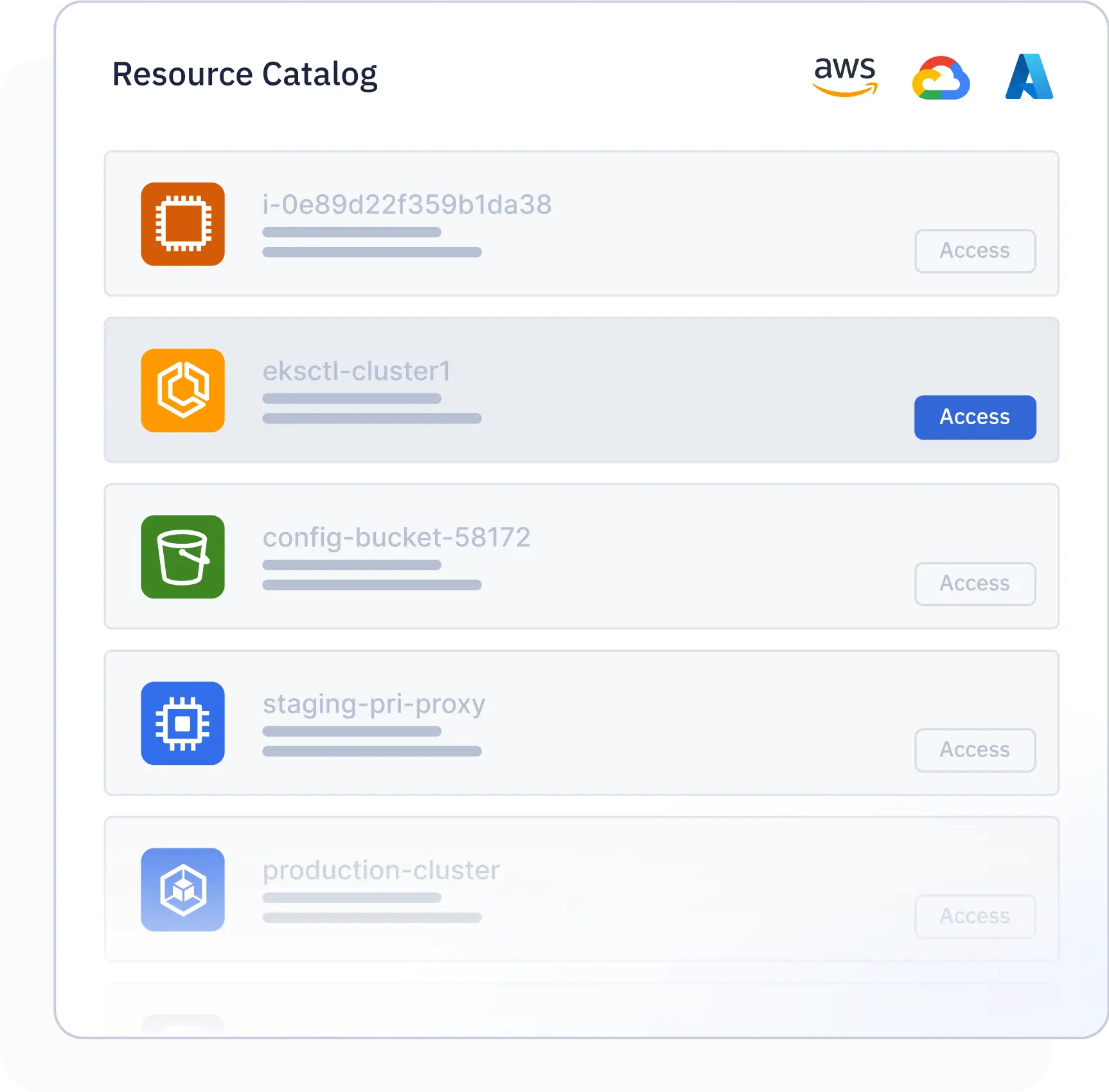
Built for Self-Service
Out of the Box Support for Multi-Cloud Infrastructure
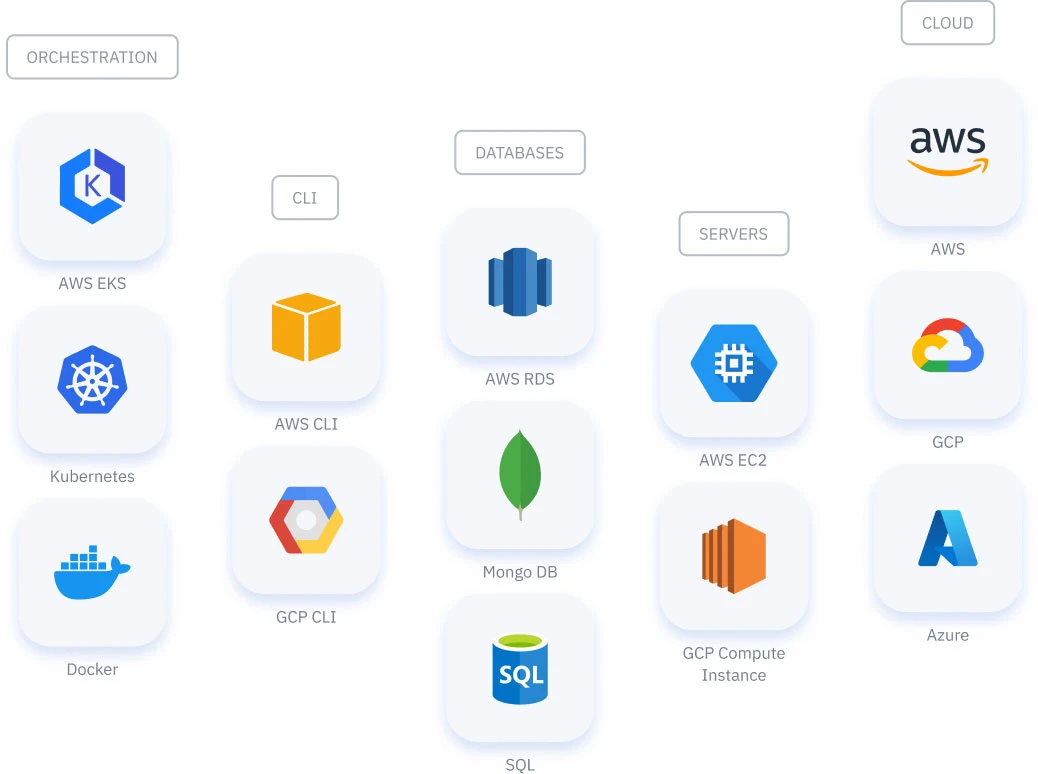

Out of the Box Support for Multi-Cloud Infrastructure

Compliance and Governance
The Procyon Difference
 Cloud Native Architecture
Cloud Native Architecture
Deep integration with all 3 cloud providers leveraging cloud native APIs
 Trusted Platform Module
Trusted Platform Module
Every access is cryptographically signed for hardened protection
 Compliance and Governance
Compliance and Governance
Maintains the strictest visibility and governance requirements
 Self-service Portal
Self-service Portal
Enables a swift yet robust grant approval process for DevOps
 Decentralized Approval System
Decentralized Approval System
Creates an efficient, cloud-centric workflow across local DevOps

Procyon collaborates with independent professionals to validate its security, privacy, and compliance measures, and has successfully obtained a SOC 2 Type 2 report that meets rigorous criteria.
Ready To Get Started?
Gain control of your sensitive data in the cloud.
Recent Resources
Get in touch
Want to know more about our product? Please fill out the form and share your message with us.
- Request a demo
- Business tiers and pricing
- General questions


