Procyon Blog
Everything you need to know about cloud and user identity
The Sisense Breach: Why Strengthening Credential Security is Priority In today's interconnected digital landscape, cybersecurity breaches have...
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and discretionary...
Image credit: Unsplash Passkeys are emerging as a popular passwordless phishing resistant authentication technology. Passkey is a friendly brand...
Image credit: Unsplash Ken Thompson the creator of Unix operating system and C programming language gave his now famous Turing award acceptance...
Image credit: Unsplash In the previous blog post, we discussed how to protect against the compromise of highly privileged human users. In this post...
Image credit: Unsplash Protecting highly privileged users is at the heart of security 2.0 stack. Easiest way to become the source of a software...
Image credit: Unsplash We are a mid-sized startup and our code base is little over a million lines of code. If we include all the packages we import...
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Unmasking Hidden Risks: A Proactive Guide to Strengthening Your IAM Framework
Introduction Every login, password reset, or system access request introduces potential risks to your Identity and Access Management (IAM)...
Access Granted: 2024’s Defining Trends in Identity and Access Management
As 2024 wraps up, it’s clear that access management has been anything but static this year. From relentless cyber threats to game-changing tech...
Top Reasons to Implement Identity and Access Management
With cyber threats reaching unprecedented levels and regulatory standards tightening worldwide, organizations are rethinking their approach to...
Preparing for 2025: Why Identity and Access Management Should Be A Top Priority
As we approach 2025, cybersecurity threats are evolving faster than ever. Identity-based attacks, such as phishing, credential stuffing, and insider...
Governance vs. Management? Navigating Identity Strategies
Introduction In today’s fast-evolving digital landscape, the question of whether to focus on governance or management in identity and access...
RIP Legacy PAM: The Era of Cloud Privilege Access Management is Here to Stay!
Managing access to cloud infrastructure has become one of the most critical security challenges for businesses today. Platforms like AWS, GCP,...
From Chaos to Control: Mastering Access Privileges in Hybrid Environments
Let’s get real: managing access privileges in today’s hybrid environments is like trying to navigate a maze blindfolded. With organizations...
Navigating RBAC: A Kubernetes Access Management Checklist
In the world of Kubernetes, managing access and permissions is not just a best practice—it’s a necessity. With the rise of container orchestration,...
From Zero Trust to Zero Standing Privileges: Strengthening Cyber Defense
As cyber threats grow more sophisticated, organizations are realizing that old-school security models just don’t cut it anymore. To tackle this...
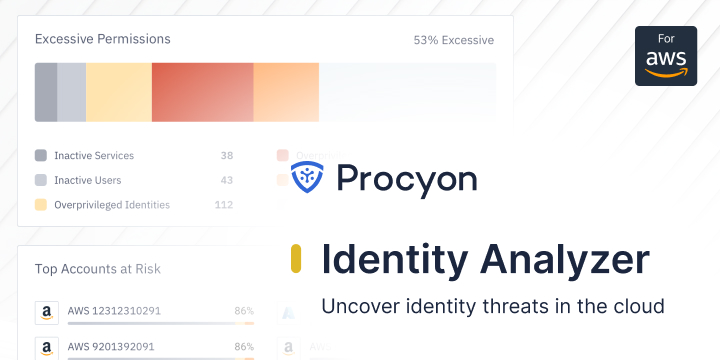
The Cost of Overprivileged Access: Why You Can’t Afford to Ignore It
Where every click can lead to a potential security breach, understanding access management isn’t just a tech problem—it’s a business imperative....
Securing the Cloud, One Stein at a Time: Oktoberfest Celebrates Cybersecurity Awareness Month
As the leaves turn golden and the sound of festive cheers fills the air, it’s not just beer lovers who are in celebration mode—cybersecurity...
Mastering User Access Reviews: A Compliance Playbook
In a world where data breaches dominate headlines and regulatory scrutiny intensifies, user access reviews have emerged as a critical line of...
Unmasking Hidden Risks: A Proactive Guide to Strengthening Your IAM Framework
Introduction Every login, password reset, or system access request introduces potential risks to your Identity and Access Management (IAM)...
Access Granted: 2024’s Defining Trends in Identity and Access Management
As 2024 wraps up, it’s clear that access management has been anything but static this year. From relentless cyber threats to game-changing tech...
Top Reasons to Implement Identity and Access Management
With cyber threats reaching unprecedented levels and regulatory standards tightening worldwide, organizations are rethinking their approach to...
Preparing for 2025: Why Identity and Access Management Should Be A Top Priority
As we approach 2025, cybersecurity threats are evolving faster than ever. Identity-based attacks, such as phishing, credential stuffing, and insider...
Governance vs. Management? Navigating Identity Strategies
Introduction In today’s fast-evolving digital landscape, the question of whether to focus on governance or management in identity and access...
RIP Legacy PAM: The Era of Cloud Privilege Access Management is Here to Stay!
Managing access to cloud infrastructure has become one of the most critical security challenges for businesses today. Platforms like AWS, GCP,...
From Chaos to Control: Mastering Access Privileges in Hybrid Environments
Let’s get real: managing access privileges in today’s hybrid environments is like trying to navigate a maze blindfolded. With organizations...
Navigating RBAC: A Kubernetes Access Management Checklist
In the world of Kubernetes, managing access and permissions is not just a best practice—it’s a necessity. With the rise of container orchestration,...
From Zero Trust to Zero Standing Privileges: Strengthening Cyber Defense
As cyber threats grow more sophisticated, organizations are realizing that old-school security models just don’t cut it anymore. To tackle this...
The Cost of Overprivileged Access: Why You Can’t Afford to Ignore It
Where every click can lead to a potential security breach, understanding access management isn’t just a tech problem—it’s a business imperative....
Securing the Cloud, One Stein at a Time: Oktoberfest Celebrates Cybersecurity Awareness Month
As the leaves turn golden and the sound of festive cheers fills the air, it’s not just beer lovers who are in celebration mode—cybersecurity...
Mastering User Access Reviews: A Compliance Playbook
In a world where data breaches dominate headlines and regulatory scrutiny intensifies, user access reviews have emerged as a critical line of...
Unmasking Hidden Risks: A Proactive Guide to Strengthening Your IAM Framework
Introduction Every login, password reset, or system access request introduces potential risks to your Identity and Access Management (IAM)...
Access Granted: 2024’s Defining Trends in Identity and Access Management
As 2024 wraps up, it’s clear that access management has been anything but static this year. From relentless cyber threats to game-changing tech...
Top Reasons to Implement Identity and Access Management
With cyber threats reaching unprecedented levels and regulatory standards tightening worldwide, organizations are rethinking their approach to...
Preparing for 2025: Why Identity and Access Management Should Be A Top Priority
As we approach 2025, cybersecurity threats are evolving faster than ever. Identity-based attacks, such as phishing, credential stuffing, and insider...
Governance vs. Management? Navigating Identity Strategies
Introduction In today’s fast-evolving digital landscape, the question of whether to focus on governance or management in identity and access...
RIP Legacy PAM: The Era of Cloud Privilege Access Management is Here to Stay!
Managing access to cloud infrastructure has become one of the most critical security challenges for businesses today. Platforms like AWS, GCP,...
From Chaos to Control: Mastering Access Privileges in Hybrid Environments
Let’s get real: managing access privileges in today’s hybrid environments is like trying to navigate a maze blindfolded. With organizations...
Navigating RBAC: A Kubernetes Access Management Checklist
In the world of Kubernetes, managing access and permissions is not just a best practice—it’s a necessity. With the rise of container orchestration,...
From Zero Trust to Zero Standing Privileges: Strengthening Cyber Defense
As cyber threats grow more sophisticated, organizations are realizing that old-school security models just don’t cut it anymore. To tackle this...
The Cost of Overprivileged Access: Why You Can’t Afford to Ignore It
Where every click can lead to a potential security breach, understanding access management isn’t just a tech problem—it’s a business imperative....
Securing the Cloud, One Stein at a Time: Oktoberfest Celebrates Cybersecurity Awareness Month
As the leaves turn golden and the sound of festive cheers fills the air, it’s not just beer lovers who are in celebration mode—cybersecurity...
Mastering User Access Reviews: A Compliance Playbook
In a world where data breaches dominate headlines and regulatory scrutiny intensifies, user access reviews have emerged as a critical line of...
Unmasking Hidden Risks: A Proactive Guide to Strengthening Your IAM Framework
Introduction Every login, password reset, or system access request introduces potential risks to your Identity and Access Management (IAM)...
Access Granted: 2024’s Defining Trends in Identity and Access Management
As 2024 wraps up, it’s clear that access management has been anything but static this year. From relentless cyber threats to game-changing tech...
Top Reasons to Implement Identity and Access Management
With cyber threats reaching unprecedented levels and regulatory standards tightening worldwide, organizations are rethinking their approach to...
Preparing for 2025: Why Identity and Access Management Should Be A Top Priority
As we approach 2025, cybersecurity threats are evolving faster than ever. Identity-based attacks, such as phishing, credential stuffing, and insider...
Governance vs. Management? Navigating Identity Strategies
Introduction In today’s fast-evolving digital landscape, the question of whether to focus on governance or management in identity and access...
RIP Legacy PAM: The Era of Cloud Privilege Access Management is Here to Stay!
Managing access to cloud infrastructure has become one of the most critical security challenges for businesses today. Platforms like AWS, GCP,...
From Chaos to Control: Mastering Access Privileges in Hybrid Environments
Let’s get real: managing access privileges in today’s hybrid environments is like trying to navigate a maze blindfolded. With organizations...
Navigating RBAC: A Kubernetes Access Management Checklist
In the world of Kubernetes, managing access and permissions is not just a best practice—it’s a necessity. With the rise of container orchestration,...
From Zero Trust to Zero Standing Privileges: Strengthening Cyber Defense
As cyber threats grow more sophisticated, organizations are realizing that old-school security models just don’t cut it anymore. To tackle this...
The Cost of Overprivileged Access: Why You Can’t Afford to Ignore It
Where every click can lead to a potential security breach, understanding access management isn’t just a tech problem—it’s a business imperative....
Securing the Cloud, One Stein at a Time: Oktoberfest Celebrates Cybersecurity Awareness Month
As the leaves turn golden and the sound of festive cheers fills the air, it’s not just beer lovers who are in celebration mode—cybersecurity...
Mastering User Access Reviews: A Compliance Playbook
In a world where data breaches dominate headlines and regulatory scrutiny intensifies, user access reviews have emerged as a critical line of...