Procyon Blog
Everything you need to know about cloud and user identity
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
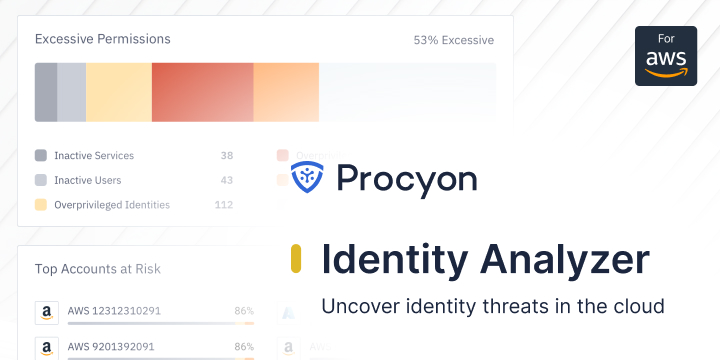
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Credential Compromise: The #1 Silent Threat to Organizational Security
In today's relentless cyber threat landscape, one challenge stands out as the predominant factor behind security breaches: credential compromise. As...
Is Best-of-Suite Cybersecurity the Future, or Will Best-of-Breed Continue To Rule?
Many CISOs make decisions based on finding a perfect balance between business and security. Their role involves protecting both the employees and...
How Will Generative AI Impact Identity and Privilege Access Management?
Generative AI can significantly enhance cybersecurity, especially in Identity and Access Management (IAM) and Privilege Access Management (PAM)....
Just-In-Time Access?
Just-in-time (JIT) access is a security approach where access to resources is granted only when needed and for a limited time with Just Enough...
What is Modern Privileged Access Management ?
Privileged Access Management (PAM) is a set of principles and practices to control, monitor, and secure access to critical resources by human and...
Uber breach 2022: What do we know and how to prevent it
On Thursday September 15 news broke out that Uber’s internal systems were breached. Our sympathies are with Uber’s security team. Uber has one of...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Credential Compromise: The #1 Silent Threat to Organizational Security
In today's relentless cyber threat landscape, one challenge stands out as the predominant factor behind security breaches: credential compromise. As...
Is Best-of-Suite Cybersecurity the Future, or Will Best-of-Breed Continue To Rule?
Many CISOs make decisions based on finding a perfect balance between business and security. Their role involves protecting both the employees and...
How Will Generative AI Impact Identity and Privilege Access Management?
Generative AI can significantly enhance cybersecurity, especially in Identity and Access Management (IAM) and Privilege Access Management (PAM)....
Just-In-Time Access?
Just-in-time (JIT) access is a security approach where access to resources is granted only when needed and for a limited time with Just Enough...
What is Modern Privileged Access Management ?
Privileged Access Management (PAM) is a set of principles and practices to control, monitor, and secure access to critical resources by human and...
Uber breach 2022: What do we know and how to prevent it
On Thursday September 15 news broke out that Uber’s internal systems were breached. Our sympathies are with Uber’s security team. Uber has one of...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Credential Compromise: The #1 Silent Threat to Organizational Security
In today's relentless cyber threat landscape, one challenge stands out as the predominant factor behind security breaches: credential compromise. As...
Is Best-of-Suite Cybersecurity the Future, or Will Best-of-Breed Continue To Rule?
Many CISOs make decisions based on finding a perfect balance between business and security. Their role involves protecting both the employees and...
How Will Generative AI Impact Identity and Privilege Access Management?
Generative AI can significantly enhance cybersecurity, especially in Identity and Access Management (IAM) and Privilege Access Management (PAM)....
Just-In-Time Access?
Just-in-time (JIT) access is a security approach where access to resources is granted only when needed and for a limited time with Just Enough...
What is Modern Privileged Access Management ?
Privileged Access Management (PAM) is a set of principles and practices to control, monitor, and secure access to critical resources by human and...
Uber breach 2022: What do we know and how to prevent it
On Thursday September 15 news broke out that Uber’s internal systems were breached. Our sympathies are with Uber’s security team. Uber has one of...
Do your DevOps & SRE teams have too much Access to your Infrastructure?
Procyon's Multi-cloud Privilege Access Management Can Help As you may be aware, managing access to cloud-based infrastructure is becoming...
Significance of TPM in Ensuring Enterprise Security
Trusted Platform Module (TPM) is a specialized hardware chip in modern computers that properly isolate sensitive operations: key management (key...
How Passwords are Weakening Your Cybersecurity
The Problem With Passwords Passwords have long served as the foundation of cybersecurity, allowing users to access their personal information...
Identity Analyzer — Now, cloud IAM teams can uncover identity threats
The first step to securing your cloud infrastructure is securing your identities. Securing identities is far more complex than it seems on...
Static Credentials and the Dilemma of Choosing Between Convenience and Security
Imagine it: A security breach has taken place in your public cloud, and while you don’t yet know how the hacker infiltrated, you know that the vast...
Credential Compromise: The #1 Silent Threat to Organizational Security
In today's relentless cyber threat landscape, one challenge stands out as the predominant factor behind security breaches: credential compromise. As...
Is Best-of-Suite Cybersecurity the Future, or Will Best-of-Breed Continue To Rule?
Many CISOs make decisions based on finding a perfect balance between business and security. Their role involves protecting both the employees and...
How Will Generative AI Impact Identity and Privilege Access Management?
Generative AI can significantly enhance cybersecurity, especially in Identity and Access Management (IAM) and Privilege Access Management (PAM)....
Just-In-Time Access?
Just-in-time (JIT) access is a security approach where access to resources is granted only when needed and for a limited time with Just Enough...
What is Modern Privileged Access Management ?
Privileged Access Management (PAM) is a set of principles and practices to control, monitor, and secure access to critical resources by human and...
Uber breach 2022: What do we know and how to prevent it
On Thursday September 15 news broke out that Uber’s internal systems were breached. Our sympathies are with Uber’s security team. Uber has one of...