The first step to securing your cloud infrastructure is securing your identities.
Securing identities is far more complex than it seems on the surface. AWS, GCP, and Azure each provide more than 1K+ predefined roles, 10K+ permissions & API endpoints to manage. If your enterprise has tens of cloud accounts, tens to hundreds of thousands of resources, finding out who has access to what and how did one get access can be a tough task. If you’re responsible for keeping track of all these and securing your environment, that’s a lot to stay on top of.
Check out cloud permissions: AWS, GCP, Azure.
Enterprises have dedicated teams for cloud IAM operations. They periodically review permissions and role definitions to rightsize. Each cloud service provider has its own permission sets and policy language. To effectively use the potential of the tens of thousands of permissions & policy language offered by CSPs (cloud service providers), a cloud IAM administrator needs to master the policies linguistics provided by the CSPs they use.
The goal is to rightsize the permissions for an identity (human or machine) for time-bound access to protect the enterprise data & resources from breaches and meet compliance requirements while keeping up the developer productivity. Digging deeper, one will realize that implementing Just-In-Time or Least Privileged access is an enormous task. IAM teams end up creating custom roles, patching existing processes for approvals, creating new workflows and building new tools. IAM operations undergo a transformation, plunging into an endless abyss of challenges. And you add more people to solve the problem.
And the uber question still stands – How are identities getting toxic or unintended permissions? What permissions are granted vs. used? Teams often spend tens of hours case by case to understand how one ended up with a particular set of permission grants. Is it through a group policy, privilege escalation, trust relationship, role chaining, or automation workflow?
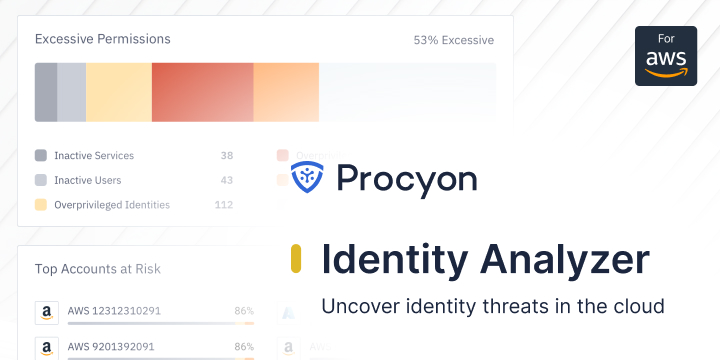
Introducing Identity Analyzer for cloud IAM teams
Today, we are delighted to unveil our latest innovation: the Identity Analyzer. Identity Analyzer is available now for AWS, and we will be releasing support for Azure and GCP in the coming weeks.
This powerful tool empowers you to visualize, identify, prioritize, and resolve potential identity threats. It’s free, and you can sign up here.