Simplify Workload IAM with Federation
Scale Workloads Without Sacrificing Security, Compliance, or Business Requirements
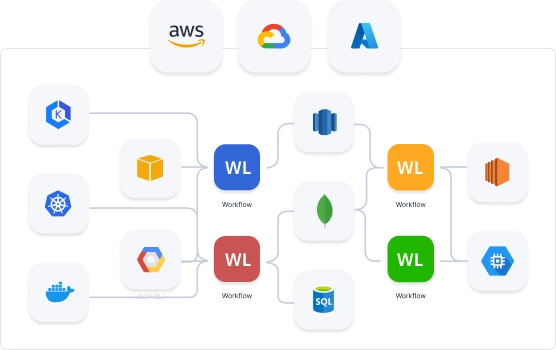
Streamline Workload Identity Federation
Give identities to workloads and manage workloads at scale.
The number of workloads typically outnumbers humans by a factor of 10 to 50 in an organization. Workload Identity Federation streamlines managing workload lifecycles and access controls through centralized management, saving developers hundreds of hours by eliminating the need for DIY IAM solutions. It simplifies development, enabling rapid adaptation to business needs.
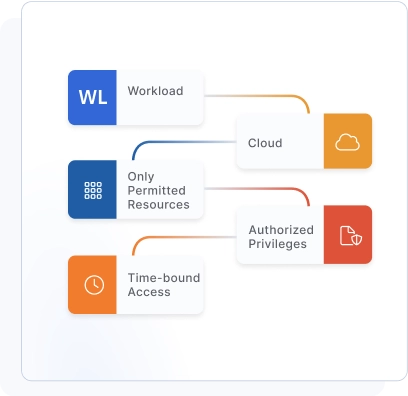
Authorize Access Through Policies
Move access control from secrets to identity-based policies.
Long-lived static credentials such as OAuth tokens, API keys, service accounts, secrets and other programmable access credentials are hard to scale, govern and secure. Instead, manage access through policies. Policies allow workloads time-bound access to resources with least-privileged access permissions.
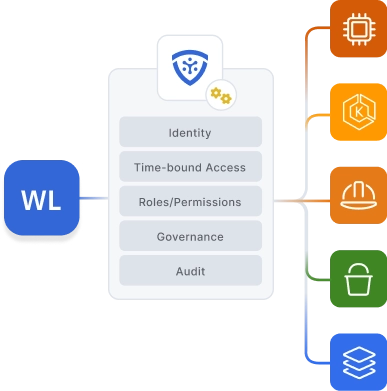
Ensure Stronger Security
Remove the overhead of managing static credentials.
Defending against static credentials embedded in workloads is an operational burden. Credential theft, service account abuse, unauthorized access, insufficient key rotation, and over-privileged access are constant threats to modern enterprises. Instead, utilize automation to provide workloads with short-lived, identity-based credentials, removing concerns for both developers and security teams.
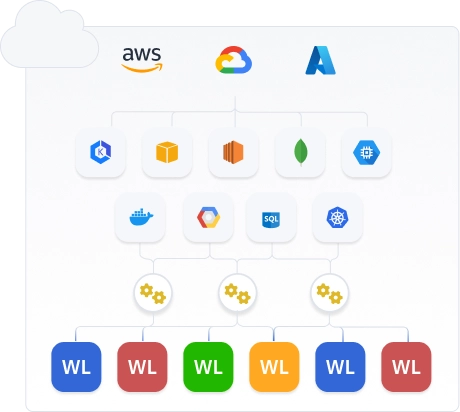
Simplify Multi-Cloud Access
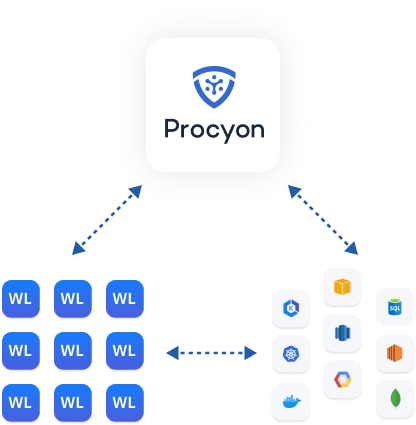
Seamless experience for managing workloads across multiple clouds.
AWS, GCP, and Azure each provide more than 10K+ permissions & API endpoints to manage. Further, each CSP has its own policy syntax. Provisioning a workload with access grants to resources & services across these clouds is an overwhelming task. Procyon solution brings in a seamless multi-cloud experience for both developers and administrators.
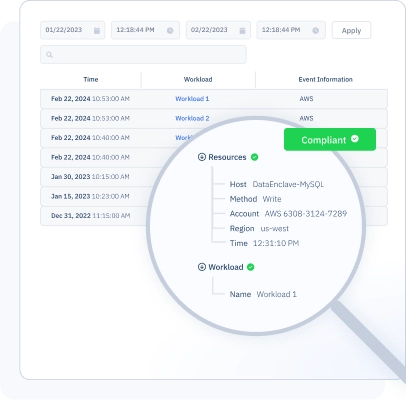
Achieve Compliance Requirements
Meet your compliance requirements for all workloads.
The dynamic nature of the cloud makes it more difficult to track and monitor workload access. With Procyon, GRC teams can easily map your compliance controls for CIS, HIPAA, ISO, SOC 2, PCI DSS, etc. to workload identity policies, audit every workload access, review grants and right-size permissions through policy controls.
How vulnerable is your organization to credential sprawl?
Discover potential vulnerabilities now with our Assessment tool and understand how Procyon can help you solve the problem in a matter of hours.
Recent Resources
The Sisense Breach: Why Strengthening Credential Security is Priority In today's interconnected digital landscape, cybersecurity breaches have...
Identity and access management traces its roots back to the mainframe era. DoD first employed logical access controls by mandatory and discretionary...
Get in touch
Want to know more about our product? Please fill out the form and share your message with us.
- Request a demo
- Business tiers and pricing
- General questions